Meet Nisos—Human Risk Intelligence Experts
We help security teams identify, investigate, and prevent human-driven threats before they escalate.
What Makes Nisos Different?
Nisos focuses on the human factor of threat intelligence. Our human risk and threat intelligence services get to the ‘who’ behind threats. Our team provides in-depth ‘outside-the-wire’ visibility as threats emerge, so you can mitigate risks before they escalate. We empower enterprises to prevent and take real-world action on human-driven threats.
The Nisos Approach to Human Risk Management
As digital and human risks converge, we deliver the who, what, why, and how of human-driven threats to protect your organization, workforce, and reputation from business risk.
Outside-In Intelligence
This outside-the-wire intelligence roots out the ‘who’ behind threats to your executives, and helps ensure you know that those you hire are who they say they are.
Expert-Led Investigations
In-depth analysis, adversary engagement, and a full threat understanding -including attribution and recommended next steps – set Nisos human risk intelligence solutions apart.
Real-world Impact
We deliver in-depth, actionable intelligence – often attributing threat actors, mapping their ecosystems, and laying bare their techniques. This provides the evidence you need to protect your organization and people, and pursue legal or law-enforcement actions.
We work together to ensure your safety
This is a core value that underscores how we apply teamwork to solve your human risk problems. In fact, we have an internal code-word for this, ‘Dogpile Collaboration’.
“We bring the unique perspective of diverse and talented operations including skills in offensive and defensive cybersecurity; open source, geospatial, signals, and human intelligence; data science, devops; and language and geopolitical SMEs. When you connect that with passion for the mission, it enables Nisos to solve hard problems for our clients.”
Landon Winkelvoss, Co-founder and VP of Legal and Intelligence Advisory
Intelligence That Works for You
At Nisos, we provide unparalleled access to difficult-to-obtain intelligence, enabling you to detect, investigate, and mitigate human risk before they impact your business.
We combine analyst-led white-glove services with a software platform to put our tradecraft directly in your hands.
Expertise in Action
The key to our human risk intelligence is our people. Our analysts are fluent in open source adversary tradecraft, threat domains, global languages and cultures, and other human risk factors that help them adeptly navigate all corners of the internet to unmask threats.
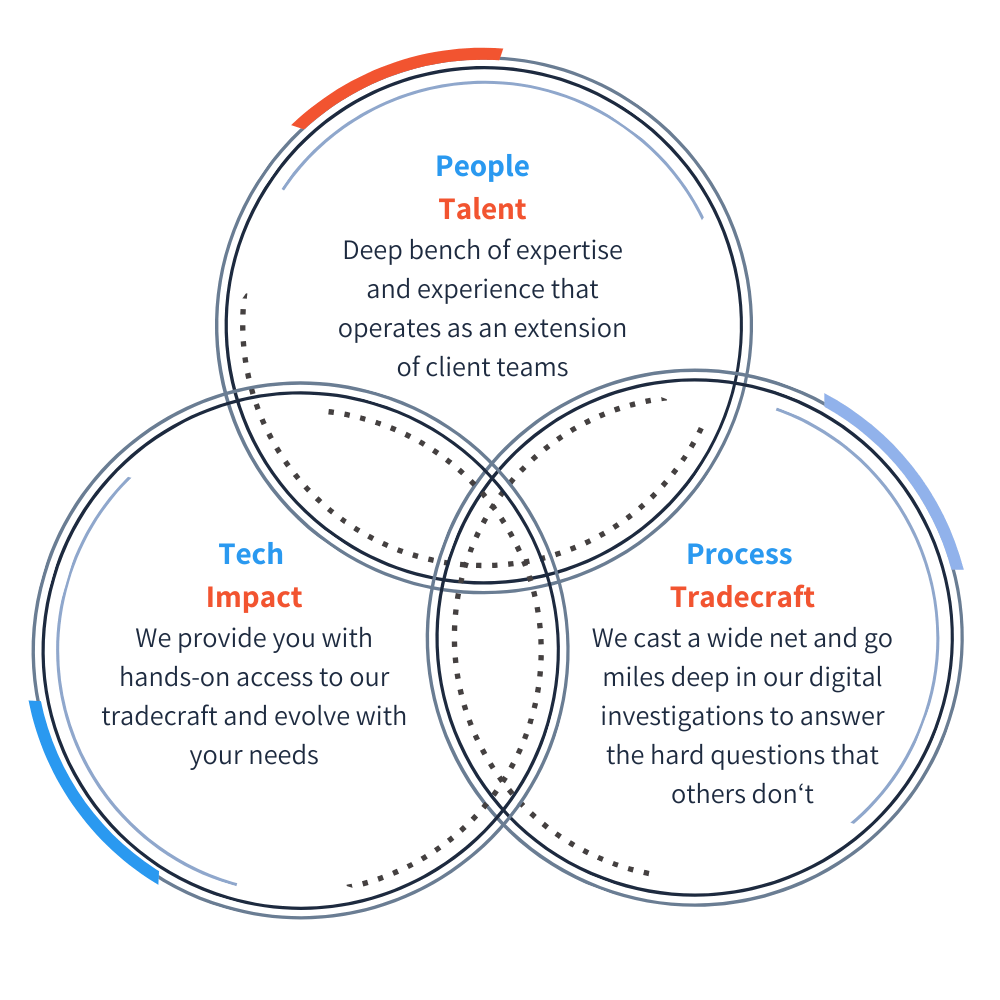
The Nisos Difference
People: Our team has a deep bench of expertise and experience that operates as an extension of your team
Technology: We scale to make open-source intelligence accessible to you and evolve with your needs.
Tradecraft: We cast a wide net and go miles deep in our digital investigations to solve problems that others don’t.