Threat Analysis
How To Proactively Mitigate The DPRK IT Worker Employment Scam
Executive Summary
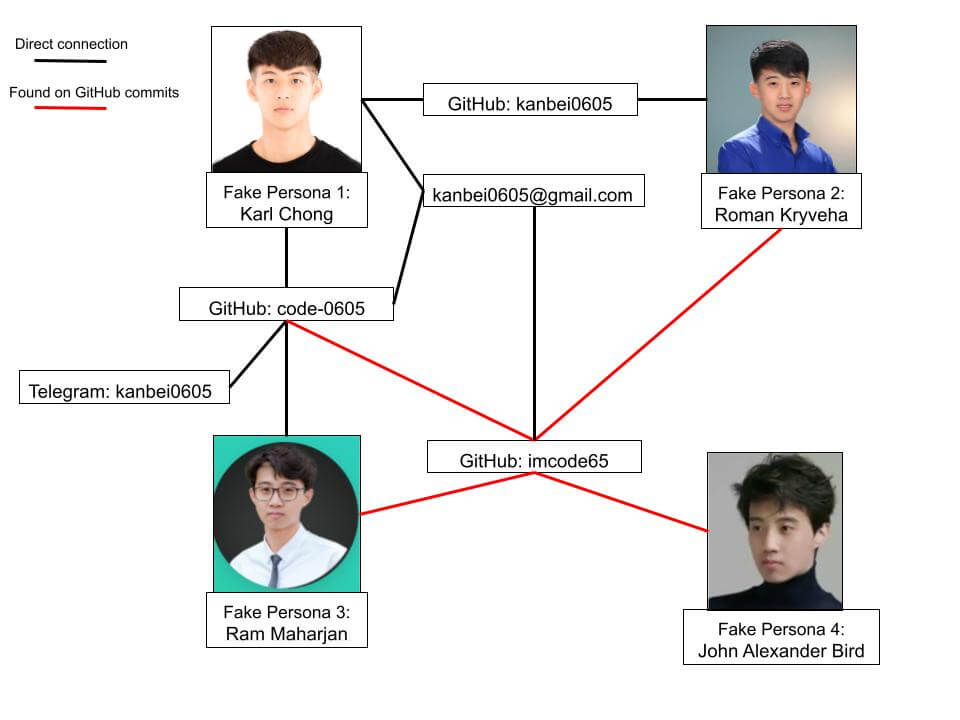
Nisos is tracking a network of likely North Korean (DPRK)-affiliated IT workers posing as Singaporean, Turkish, Finnish and US nationals with the goal of obtaining employment in remote IT, engineering, and full-stack blockchain positions. Through our research and client work we have detected and identified a number of fake personas since 2023. Successful mitigation of the risk relies on an improved vetting process for external remote candidates, which heavily relies on open-source intelligence (OSINT) checks of portfolio content and contact information, as the network re-uses this information. To assist security teams and business leaders with protecting their organizations and their clients, Nisos provides several steps that we recommend businesses implement in their hiring process to mitigate the DPRK-affiliated IT worker threat. Nisos also provides examples of how we used OSINT to identify four active fake personas. Karl Chong, currently appears to be employed as an engineer at a US-based strategic digital consultancy company. Two additional fake personas, Roman Kryveha and Ram Maharjan, who share contact information with Karl Chong, were likely created to also obtain remote employment as part of the employment scheme. Nisos also identified a fourth fake persona, John Alexander Bird, whose resume was created and updated via GitHub account imcode65 in 2024. This persona does not have an active personal website, suggesting that it is likely not actively seeking employment as part of the employment scheme yet.
Risk Mitigation Steps
The DPRK IT worker scheme is pervasive and targets companies of all sizes and in numerous industries, including cybersecurity. Learning opportunities for enterprise leaders include the following, which we recommend communicating to HR and IT teams within the organization:
- Conduct reverse image searches to identify digitally manipulated profile pictures.
- Conduct expeditious OSINT checks to verify whether the provided phone numbers, email addresses, and GitHub accounts belong to the applicant and/or have been associated with other individuals.
- Review phone numbers and email addresses to determine whether applicants applied using the same contact information.
- Review stylometric attributes of the resume content to determine whether other resumes include the same language.
- Verify that locations match for all accounts linked to the applicant.
- Conduct a detailed review of the applicant’s online presence for consistency in name, appearance, work history, education, and other biographical details.
- Verify prior employment. Applicants often list major companies in their employment history, likely both to inflate their experience and to deter the hiring organization from contacting their provided references.
- Verify educational claims by contacting the institution’s registrar office.
- Collect and retain all contact information for the references reviewed by HR in relation to the job applicant. References are often the same individual or connected to the same network of people as the job applicant.
- Ensure the interview process involves on-camera and/or in-person interviews.
Nisos researchers were able to identify four active personas by researching GitHub account activity and cross referencing contact information and profile photos. Nisos solely used OSINT checks and did not rely on proprietary tools or paid third party subscription tools.
Fake Persona Network
Nisos identified one persona, Karl Chong, who appears to have gained employment and three newly created personas seeking remote positions in Singapore, Turkey, Finland, and the United States. The newly created personas were all created and updated in 2024 in repositories linked to GitHub account imcode65. The account is associated with the email address kanbei0605@gmail[.]com, which is also associated with the persona Karl Chong.
Karl Chong
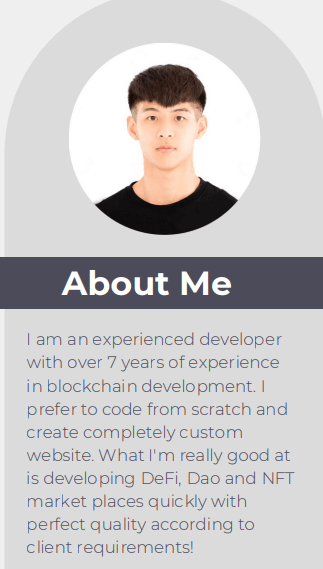
Nisos identified Karl Chong—used by a likely DPRK IT worker to obtain remote work in the United States—by investigating the GitHub account superredstar, which Nisos previously linked to a likely DPRK-affiliated network of remote worker personas. [1] The GitHub account superredstar was used to create a resume website for Karl Chong via GitHub in April 2022.[2] Karl Chong claims to be from Singapore and appears to be employed as a remote MERN Stack Developer at US-based Mongrov Inc since May 2023. Karl Chong has several freelancer accounts, which claim that he is located in the United States and Turkey. A review of the Karl Chong accounts and website revealed several tactics, techniques, and procedures (TTPs) previously associated with the DPRK employment scheme, including fake profile pictures, a lack of consistency of information across all accounts, the persona claiming to have experience developing web and mobile applications, knowledge of multiple programming languages, and reused resume content from other personas.
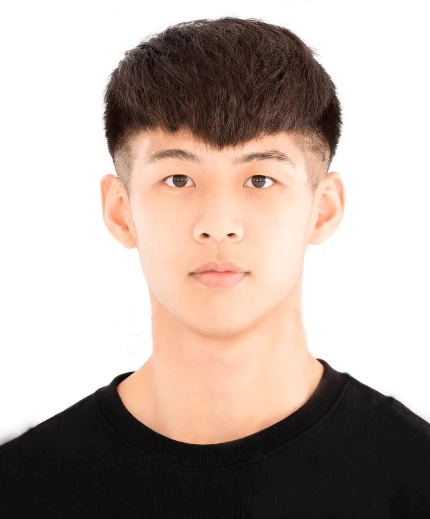
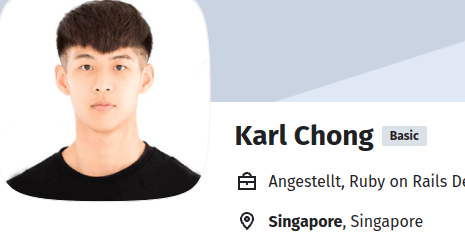
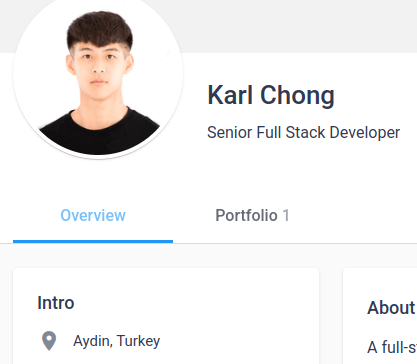
Fake Profile Photo
Karl Chong’s website and freelancer accounts use the photo featured in Graphics 2-4, which is available for purchase on a number of stock photo websites. Nisos assesses that likely DPRK IT workers used this method to hide their true identities before using possible AI-enabled tooling to merge their faces onto pictures of other individuals.
Misaligned locations
Karl Chong claims to be located in Singapore, the United States, and Turkey on his various online resumes. Nisos assesses that the same persona is used to seek employment in different countries, which is why the persona’s stated locations vary.
Reused Resume Content
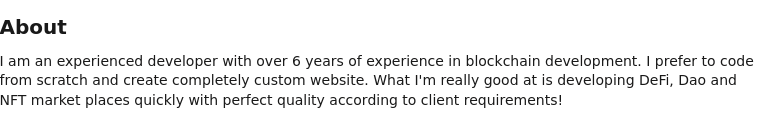
Nisos found that Karl Chong’s resume referenced the same employment history as another likely DPRK-affiliated persona, Naoyuki Tanaka, who appears to have been employed at Enver Studio. [9] Nisos assesses that likely DPRK IT workers reuse GitHub accounts and work portfolios to backstop their newly created personas. Additionally, another fake persona, Roman Kryveha, reused Karl Chong’s about me intro paragraph from his resume and his stock photo.
Significant Development Experience
Karl Chong lists a number of programming languages and certificates on his website. He also claims to have seven years of experience in front and back-end web development.
Freelancer Employment Websites Linked To Karl Chong
Nisos identified four freelance employment websites, which listed the persona name, location, GitHub, and work history of the persona. Many of the resumes indicated that Karl Chong worked at Overflow and studied at Singapore University of Technology and Design. The persona’s profiles on freelancer websites include:
- https://remoteok[.]com/@karlchong
- https://laborx[.]com/freelancers/users/id100369
- https://www.remotehub[.]com/karl.chong
- https://www.xing[.]com/profile/Karl_Chong
About Nisos®
Nisos is the Managed Intelligence Company. We are a trusted digital investigations partner, specializing in unmasking threats to protect people, organizations, and their digital ecosystems in the commercial and public sectors. Our open source intelligence services help security, intelligence, legal, and trust and safety teams make critical decisions, impose real world consequences, and increase adversary costs. For more information, visit: https://nisos.com.