Threat Analysis
DPRK IT Worker Tradecraft Between 2022 and 2025
Executive Summary
- Advanced technology, such as Artificial Intelligence (AI) for image manipulation
- Templates for persona website creation via Github repositories
- Reused resume content
- Fake addresses
Nisos also observed DRPK IT workers quickly pivoting to other personas if a persona was fired by an employer or flagged and removed from GitHub or freelancer websites. DPRK IT workers quickly create new personal websites and freelancer accounts to continue the work the previous persona was doing.
Use of AI in Profile Images
Nisos observed increased sophistication related to how DPRK IT workers use AI to generate profile pictures for their personas. In 2022, DPRK IT workers did not include photos of themselves on their portfolio website or freelancer accounts and instead relied on cartoons to hide their true identities. Starting in 2023, DPRK IT workers began putting their faces on stock photo bodies, to make their accounts seem more legitimate. Since 2024, DPRK IT workers have used AI to combine their faces with stock images to make their profile photos appear more legitimate.
Cartoon Images
Nisos observed a number of instances of DPRK-affiliated personas using cartoons or other images to mask the true identity of the IT worker. Most of these personas were created in 2022.
Digitally Manipulated Images
Nisos observed a number of instances of digitally manipulated profile images, which combine the faces of IT workers onto stock photos. These personas were created before 2024.
AI-Manipulated Images
Nisos observed a number of instances of AI-manipulated profile images, which combine the faces of IT workers with stock photos. These personas were all created in 2024.
Templates For Websites
According to the US Office of Foreign Assets Control (OFAC), DPRK IT workers build “portfolio” websites, generally simple in design, in an effort to boost the credibility of their fabricated, freelance developer personas. These virtual portfolios represent the work of DPRK IT workers’ personas and are often linked to their online freelance developer accounts.[8] Nisos observed that DPRK IT workers began using templates to build portfolio websites for their personas in 2023. These included templates from websites such as bootstrapmade[.]com.
Bootstrapmade
Nisos observed that likely DPRK-affiliated GitHub account imcode65 created a portfolio website for a persona named John Alexander Bird importing a template from website bootstrapmade[.]com on 30 November 2023. Several other likely affiliated DPRK personas also used website templates that appear similar to the Bootstrapmade template, to post the portfolio websites on vercel[.]app. Vercel is a platform that provides developer tools and cloud infrastructure to individuals to personalize the website for them.[9]
Reused Resume Content
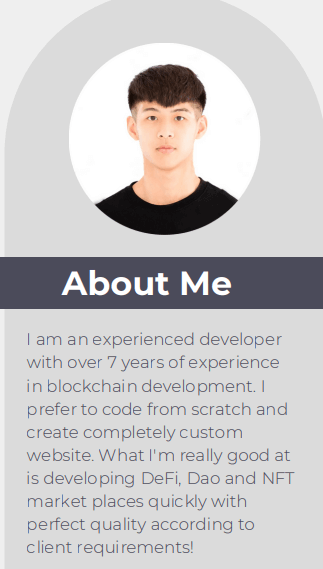
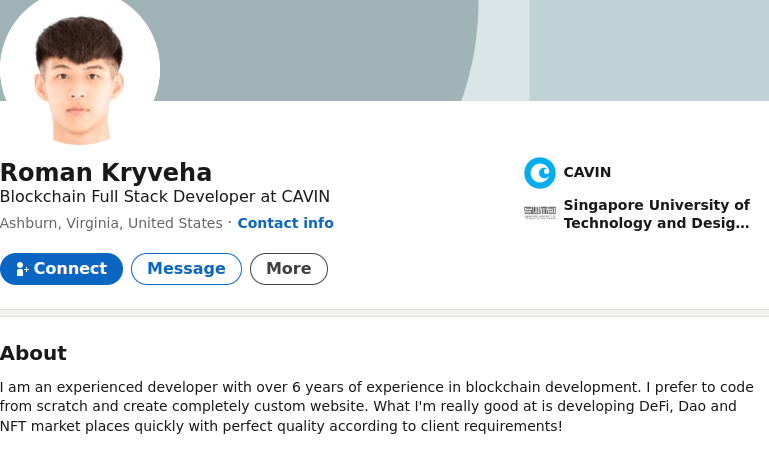
Nisos observed a number of DRPK-affiliated personas use the same or similar introduction section on their resumes. DPRK-affiliated personas Karl Chong and Roman Kryveha for example stated that they both are experienced developers with over seven years of experience in blockchain development.
GitHub Accounts
Nisos observed that GitHub accounts are re-used to backstop different personas. Nisos assesses that DPRK affiliated IT workers reuse the accounts in order to provide fake work history to their personas. GitHub account redsky500, which is no longer active, for example was associated with the personas Code Solution, CodeJourney, and Ryosuke Yamamoto. [15 16 17] Code Solution claims to be the user of redsky500 and claims to have 10 years of work experience. [18] Redsky500 is also associated with likely DPRK persona Ryosuke Yamamoto, who has six years of work experience and appears to be employed at WowDAO as a Web3 Full Stack Developer. [19] In addition to their association with the same GitHub account, Code Solution and Ryosuke Yamamoto share association with the number 0302. Code Solution lists their contact information as Telegram ID doom0302 while Ryosuke Yamamoto lists Telegram ID Ryosuke0302 and email address phantomdev0302@gmail[.]com. [20 21]
About Nisos®
Nisos is the human risk management company specializing in unmasking threats before they escalate. We are a trusted advisor who operates as an extension of security, intelligence, legal, and human resource teams to protect their people and business. Our intelligence-led solutions help enterprises make critical decisions, manage human risk, and drive real world consequences for digital threats.
For more information, visit: https://nisos.com.