Protecting Online Platforms
Protect your platform, users, and brand from human-driven threats—like coordinated abuse, digital harassment, and reputation attacks.
Ensure Safe and Compliant Spaces
UNMASK THREATS
Whether you face organized crime, nation-state campaigns, or individual actors, Nisos can unmask and attribute the threats targeting your platform.
ENABLE REAL-WORLD CONSEQUENCES
Nisos supports service providers with answers to critical security questions and provides guidance to increase adversary costs, through legal, organizational, or technical responses.
ADHERE TO GLOBAL REGULATIONS
Nisos intelligence services support DSA compliance, including risk assessments, incident response, and content flagging.
How Extremists Are Using Video Games to Spread Hate
Success Stories
IP Theft and Data Scraping
Nisos unmasks actors publishing content stolen from a top educational technology brand.
read case study >>
Extremism and Recruiting
Nisos does a deep dive into an anti-government militia recruiting on a global social media platform.
read case study >>
Targeted Disinformation
Nisos investigates threat actors behind targeted campaigns against global Healthcare technology brands.
read case study >>
Threat Monitoring
Nisos provides overwatch for a major gig economy platform whose CEO was the target of planned protests.
read case study >>
Your Trusted Digital Investigation Partner
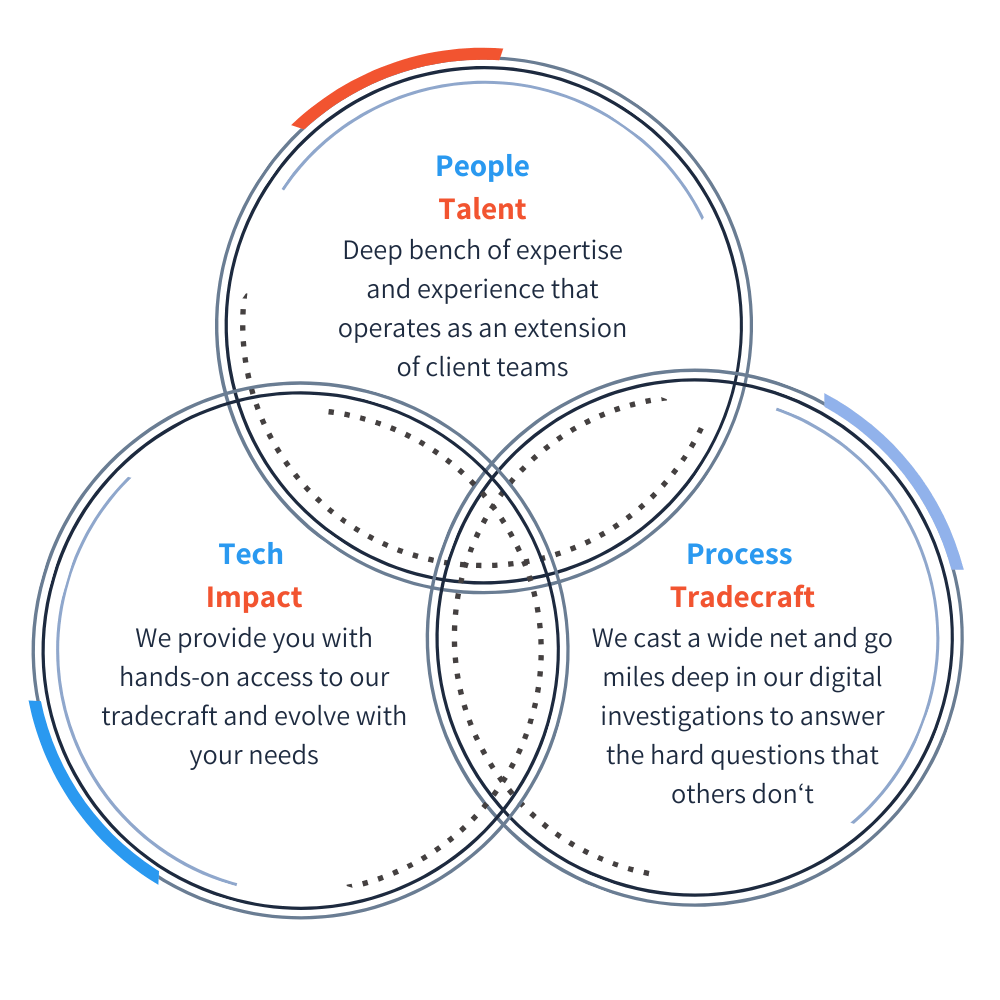
Nisos analysts operate as an extension of your team, performing critical digital investigations to tie digital footprints to real-world threats. They draw on powerful technology, deep intelligence expertise, experience, and mastery of sophisticated tradecraft to deftly navigate across platforms and the open source ecosystem to deliver the answers you need to shut down threats. We help trust and safety teams combat illicit content, uncover cyber threats, and monitor for threats of violence, with specialization in:
- Threat actor and adversary attribution
- Coordinated inauthentic behavior
- Anti-scraping
- Disinformation and misinformation
- Extremist communities, events, and recruitment
- And more…
Reduce Risk to Your Platform with Nisos
Investigations
Investigate digital threats with confidence
From receiving tailored scoping to actionable risk reduction recommendations, you have direct access to Nisos’ expert analysts and advisors. Our intelligence experts bring years of experience conducting complex investigations and intelligence operations within highly sensitive environments, helping organizations proactively manage threats and protect their communities.
Monitoring
Stay in lockstep with adversaries by measuring exposure and emerging risks
Through our analyst-driven monitoring and critical threat notifications we support your organization’s unique trust and safety needs, providing precise responses and tailored risk mitigation guidance. This approach strengthens your role as a trusted partner to internal stakeholders, including legal teams and executive leadership.
Assessments
See through the eyes of an adversary
Nisos risk assessments involve collecting and analyzing large amounts of data from digital sources beyond your platform to deliver a comprehensive cross-platform risk evaluation, and include specific, next step recommendations to proactively reduce your risk.
“Nisos has an amazing team. They have assisted us tremendously as we have grown our security capabilities over the past several years. Their ability to adapt to our needs as we mature has made them a key and critical partner for us.”
Dan Williams | Senior Manager, Physical Security – Uber Technologies, Inc
The Nisos Difference
Immediately Useful Intelligence: Actionable, real-time intelligence to enable informed and responsible decision-making that protects users and upholds platform integrity.
Intelligence Tailored to You: Aligned to your organization’s needs, priorities, policies, risks, and users. needs to deliver on your trust and safety mission.
An Extension of Your Team: Our deep bench of intelligence experts works shoulder to shoulder with you to help you deliver on your trust and safety mission.
Related Resources

Tackling influence operations (IO) in a normal year is difficult enough. This year, half the world’s population head to…

India just wrapped up the world’s largest elections during which we saw broad use of AI, offering insights for future election cycles and AI’s possible role in them.

Top 5 Social Media Content Evasion Tactics
Users spreading violative content rely on various tactics to evade content moderation on social media platforms, including to spread violent…

